Friday, 4 November 2016
Digital Image Processing — Filters
14:25
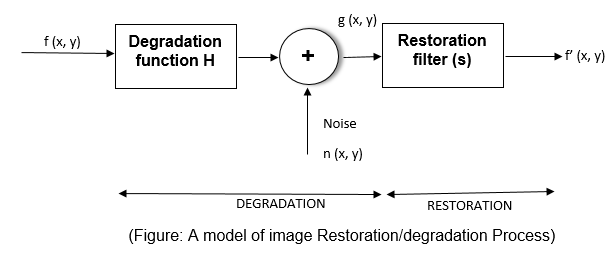
Restoration
in The Presence of Noise Only
When the only degradation present in an image noise,
equations:
g
(x, y) = f (x, y) + η (x, y)
and
G
(u, v) = F (u, v) + N (u, v)
The noise terms are unknown, so subtracting them from g (x,
y) and G (u, v) is not a realistic option. In this case N (u, v) can be
subtracted from G (u, v) to obtain an estimate N (u, v) from the spectrum of G
(u, v).
Mean
Filters: - The different types of noise reduction mean
filters are given below: -
1.
Arithmetic
Mean Filter: - This is the simplest of the mean filters. Let Sxy
represent the set of coordinates in a rectangular subimage window of
size m x n, centered at a point (x, y). The arithmetic mean filter computes the
average value of the corrupted image g
(x, y) in the area defined by Sxy. The value of the restored image f’
at point (x, y) is simply the arithmetic mean computed using the pixels in the
region defined by Sxy.
f’ (x, y) = 1/mn ∑ g (s, t)
This operation can be
implemented using a spatial filter of size m x n in which all coefficient’s
have value 1/mn. A mean filter smooth local variations in an image and noise is
reduced as a result of blurring.
2.
Geometric
Mean Filter: - An image restored using a geometric mean filter
is given by the expression
f’ (x, y) = [ π(s, t) € Sxy g (s,
t)]
Each restoration pixel is
given by the product of the pixels in the subimage window, raised to the power
1/mn. A geometric mean filter achieves smoothing comparable to the arithmetic
mean filter, but it tends to loss less image detail in the process.
3.
Harmonic
Mean Filter: - Harmonic mean filter works well for salt noise,
but fails for pepper noise. It does well also with other type of noise like
Gaussian noise.
4.
Contraharmonic
Mean Filter: - This filter is well suited for reducing or
virtually eliminating the effects of salt-and-pepper noise.
5.
Median
Filter: -The best known order statistic filter is median filter,
which is as its name implies, replaces the value of pixel by the median of the
intensity levels in the neighborhood of that pixel.
6.
Midpoint
Filter: - The midpoint filter simply computes the midpoint between
maximum and minimum values in the area encompassed by the filter. This filter
combines order statistics and averaging. It works best for randomly distributed
noise, like Gaussian or uniform noise.
7.
Inverse
Filter: - Inverse filtering is the process of recovering the input
of a system from its output. For example, in the absence of noise the inverse
filter would be a system that recovers u (m, n) from the observations v (m, n).
8.
Pseudoinverse
Filer: - It is the stabilized version of the inverse filter.
9.
The
Wiener Filter: - The main disadvantage of inverse filter and
pseudoinverse filter is that these filters remain very sensitive to noise.
Wiener filter is a method of restoring image in the presence of blur as well as
noise.
Digital Image Processing — Image Restoration Models
11:46
IMAGE RESTORATION MODELS
The principal
goal of restoration technique is to improve an image in some predefined sense.
Image restoration is concerned with filtering the observed image to minimize
the effect of degradations. Image restoration refers to removal or minimization
of known degradations in an image. This includes deblurring of images degraded
by the limitation of a sensor or its environment, noise filtering or non-linarities
due to sensors.
The
fundamental result in filtering theory used commonly for image restoration is
called the Wiener filter. This
filter gives the best linear mean square estimate of the object from the
observation. It can be implemented in frequency domain by the fast unitary transforms.
Other image restoration methods are: - least
squares, constrained least squares, and spline interpolation methods. Other
methods such as likelihood, maximum entropy, and maximum posteriori are nonlinear
techniques that require iterative solutions.
Image
Restoration Models: - There are different models of image
restoration given below:
1) Image
formation models.
2) Detector
and recorder.
3) Noise
models.
4) Sampled
observation models.
5) Detector and Recorder Models.
Here, the degradation process
is modeled as a degradation function together with an additive noise term,
operates on input image f (x, y) to produce a degraded image g (x, y). The
restoration approach is based on various types of image restoration filters.
1.
Image
Formation Model: - The
study of image formation encompasses the radiometric and geometric processes by
which 2D images of 3D objects are formed. In the case of digital images, the
image formation process also includes analog to digital conversion and
sampling.
Diffraction-limited coherent systems
have the effect of being ideal low-pass filters.
Motion blur occurs when there is
relative motion between the object and the camera during exposure. Atmospheric turbulence is due to
random variations in the refractive index of medium between the object and the
image system. Such degradation occurs in the imaging of astronomical images.
Examples of Spatially Invariant models: -
1)
Diffraction limited, coherent (with
rectangular aperture)
2)
Diffraction limited, incoherent (with
rectangular apeture)
3)
Horizontal motion
4)
Atmospheric turbulence
5)
Rectangular scanning aperture
6)
CCD interactions
2. Detector and Recorder Model: -
The
response of image detectors and recorders is generally nonlinear. For example,
the response of photographic films, image scanners, and display devices can be
written as
g =
awb
where
a and b are device-dependent constant and w is the input variable.
3. Noise Models: - The
principal source of noise in digital images arise during image acquisition or
transmission. The performance of imaging sensors is affected by a variety of
factors, such as environmental conditions during image acquisition, and by the
quality of the sensing elements themselves.
For example: In
acquiring images with a CCD camera, light levels sensor temperature are major
factors affecting the amount of noise in the resulting image.
An image transmitted using a wireless network
might be corrupted as a result of lightning or other atmospheric disturbance.
Some important Noise Probability Density
Functions: -
1)
Gaussian
noise: - Because of its mathematical tractability in both the
spatial and frequency domains, Gaussian (also called normal) noise model are used
frequently in practice. The PDF of a Gaussian random variable, z, is given by:
P(z)
= 1 /Ö2πσ
x e -(z-z’)/2σ2
2) Rayleigh
Noise
3) Erlang
(gamma) Noise
4) Exponential
Noise
5) Uniform
Noise
6) Impulse
(salt-and-pepper) Noise
7) Periodic
Noise
Wednesday, 2 November 2016
Information Security & DBMS
10:48
Database Security
Relational
Database: - Table of data consisting of rows and columns.
Each column holds a particular type of data. Each raw contain a specific value
for each column. Relational query language is used to access the database.
Elements
of Relational Database: -
1)
Primary
key: Uniquely identifies a row and consists of one or more
column names.
2)
Foreign
key: Links one table to an attributes in another.
3)
View/virtual
table: Result of a query that returns selected rows and columns
from one or more tables.
Structured
Query Language: - Developed by IBM in min-1970s. It is a standardized
language used to define, manipulate query data in relational table. SQL
statements can be used for: -
·
Create table.
·
Create / insert data into tables.
·
Create views
·
Retrieve data with query statements.
SQL Injection
Attacks: - One of the most prevalent and dangerous
network-based security threats.
·
It is designed to exploit the nature of web
application pages.
·
Sends malicious SQL commands to the database
server.
·
Most common attack goal is bulk extraction of
data.
·
Depending on the environment SQL injection can
be exploited to:
– Modify
or delete data
– Launch
denial-of-service (DoS) attacks
– Execute
arbitrary operating system commands.
Inband
Attack: - Uses
the same communication for injecting SQL code and retrieving results. The
retrieved data are presented directly in application web page.
–
Tautology: - This form of attack injects code in one or
more conditional statements so that they always evaluate to true.
–
End-of-line comment: - After injecting code into a particular field, legitimate
code that follows are nullified through usage of end of line comments.
–
Piggybacked queries: - The attacker adds additional queries beyond the
intended query, piggy-backing the attack on top of a legitimate request
Inferential Attack: - There is no actual transfer of data, but the
attacker is able to reconstruct the information by sending particular requests
and observing the resulting behavior of the Website/database server.
Include:
– Illegal/logically
incorrect queries
• This attack lets an attacker gather important
information about the type and structure of the backend database of a Web
application
• The attack is considered a preliminary,
information-gathering step for other attacks
– Blind
SQL injection
• Allows attackers to infer the data present in a
database system even when the system is sufficiently secure to not display any
erroneous information back to the attacker.
Database Access Control: - It determines
·
if the user has
access to the entire database or just portion of it.
·
What access rights the
user has (create, delete, update, read, write)
Can support a range of administrative policies:
-
1) Centralized
Administration: - Small number of
privileged users may grant and revoke access rights.
2) Ownership-based
Administration: - The creator of the
table may grant and revoke access rights to the table.
3) Decentralized
Administration: - The owner of the
table may grant and revoke authorization rights to other users, allowing them
to grant and revoke access rights to the table.
Role Based Access Control (RBAC): - Role-based
access control eases administrative burden and improves security
A database RBAC needs to provide
the following capabilities:
• Create and delete roles
• Define permissions for a role
•
Assign and cancel
assignment of users to roles
Categories of database users:
1)
Application owner: An end user who owns database objects (tables,
columns, rows) as part of an application. That is, the database objects are
generated by the application or are prepared for use by the application.
2)
End user other than application owner: An end user who operates on database
objects via a
particular application but does not own any of the database objects.
3)
Administrator: User who has administrative responsibility for
part or all of the
database.
A database
RBAC facility needs to provide the following capabilities:
• Create and delete roles.
• Define permissions for a role.
• Assign and cancel assignment of users to roles.
Statistical Databases
(SDB): - provides data of a
statistical nature such as counts and averages
–
pure statistical
database
–
ordinary database
with statistical access
• access control objective
–
provide users with
the needed information
–
without compromising
the confidentiality
• security problem is one of inference
Pure statistical database: This type of database only stores statistical data.
• An example is a census database. Typically, access
control for a pure SDB is straightforward: certain users are authorized to
access the entire database.
Ordinary database with
statistical access: This type of database contains individual entries; this is the type of database discussed so
far in this chapter. The database supports a population of nonstatistical users
who are allowed access to selected portions of the database using discretionary
access control (DAC), role-based access control (RBAC), or mandatory access
control (MAC).
Statistical Database
Security: -
·
use a characteristic
formula C
–
a logical formula
over the values of attributes
–
e.g. (Sex=Male)
AND ((Major=CS) OR (Major=EE))
·
query set X(C) of characteristic formula C, is the set of
records matching C
·
a statistical
query is a query that produces a value calculated over a query set
Tuesday, 1 November 2016
Digital Image Processing — Image Data Compression
06:04
Image Data Compression
Image compression, the art and science of reducing the
amount of data required to represent an image, is one of the most useful and
commercially successful technologies in the field of digital image processing.
To better understand the need of compact image representation, consider the
amount of data required to represent a two-hour
standard definition television movie using 720 x 480 x 24-bit pixel arrays.
A digital movie is sequence of video frames in which each frame is a full-color still image. Image
compression concerned with minimizing the number of bits required to represent
an image. The simplest and most dramatic form of data compression is:
·
Sampling
·
Bandlimited images
Where an infinite number of pixel per unit area is reduced
to one sample without any loss of information.
Application of data compression are primarily in
transmission and storage of information. Image transmission applications are in
broadcast tv, business and education.
Typical television have images have spatial resolution of
approximately 512 x 512 pixels per frame. At 8 bit per pixel per color channel
and 30 frames per second.
Applications
of data compression are: -
1) Image transmission
applications are in broadcast television, remote sensing via satellite,
military communication via aircraft, radar and sonar, teleconferencing, computer
communications.
2) Image storage is
required for educational and business documents, medical images that arises in
computer tomography (CT), magnetic resonance imaging (MRI) and digital
radiology, motion picture, weather maps, and so on.
Image data compression falls into two categories. In first category, called predictive coading, are that exploit redundancy in the data. Redundancy is characteristic related to such factor as predictability, randomness, and smoothness in the data. Techniques such as delta modulation and differential pulse code modulation fall into this category.
Image data compression falls into two categories. In first category, called predictive coading, are that exploit redundancy in the data. Redundancy is characteristic related to such factor as predictability, randomness, and smoothness in the data. Techniques such as delta modulation and differential pulse code modulation fall into this category.
In the second category, called transform coding,
compression is achieved by transforming the given image into another array such
that large amount of information is packed into small number of samples.
According to Shannon’s
noiseless coding theorem it is possible to code, without distortion. The
maximum achievable compression C, defined by
C
= average rate bit of the original raw data (B)/ average bit of the encoded
data (H + ἑ)
Pixel
Coding: -In this technique each pixel is processed
independently, ignoring the inter pixel dependencies. In PCM (pulse code
modulation) the incoming video signal is sampled, quantized and coded by a
suitable code word.
In PCM the incoming video signal is sampled, quantized, and
coded by a suitable code word. The quantized output is generally coed by a
fixed-length binary code word having B bits. Commonly, 8 bits are sufficient
for monochrome broadcast or video conferencing quality images, whereas medical
images or color video signals may require 10 to 12 bits per pixel.
The number of bits needed for visual display of images can
be reduced to 4 to 8 bits per pixel by using companding, contrast quantization
or dithering techniques.
The
Huffman Coding Algorithm: -
1) Arrange
the symbol probabilities p(i) in decreasing order and consider them as leaf
nodes of a tree.
1) While
there is more than one node:
·
Merge the two nodes with simplest probability
to form a new node whose probability is the sum of two merged nodes.
·
Arbitrarily assign 1 and 0 to each pair of
branches merging into a node.
2) Read
sequentially from the root node to the leaf node where the symbol is located.
Coding and decoding is done simply by looking up values in
a table.
Image
compression standards, formats and containers
1 .
Still
images: -
— Binary
·
CCITT Group 3
·
CCITT Group 4
·
JBIG1
·
JBIG2
·
TIFF
— Continuous
Tone
·
JPEG
·
JPEG-LS
·
JPEG-2000 (joint photographic expert group)
·
BMP
·
GIF
·
PNG (portable network graphics)
·
TIFF (tagged image file format)
Video:
-
·
DV
·
H.261
·
H.262
·
H.263
·
H.264
·
MPEG-1
·
MPEG-2
·
MPEG-4
·
AVS (audio video standard)
·
HDV (high definition video)
·
QUICK TIME
·
VC-1
Subscribe to:
Comments (Atom)